As insider-driven data breaches continue to escalate, posing severe financial and reputational risks to organizations, the need for advanced security measures is increasingly critical. G-71 Security’s invisible watermarking technology addresses this urgent problem by embedding undetectable modifications, or invisible watermarks, into documents. These watermarks are not visible to the naked eye but allow for the tracking and identification of the source of a document leak. This technology serves as a crucial line of defense in both digital and printed formats, enhancing traditional security systems and providing a robust tool against the unauthorized dissemination of confidential information. By integrating seamlessly with existing IT infrastructure, G-71’s invisible watermarking offers a proactive, scalable solution to a growing threat, making it an essential component of modern data security strategies.
In the wake of a 28% increase in insider-driven data exposure incidents as reported in Code42’s 2024 Data Exposure Report (DER), companies are urgently revisiting their security strategies. Traditional systems like Data Loss Prevention (DLP) no longer suffice on their own, highlighting the need for more comprehensive solutions, including invisible watermarking.
Invisible watermarking serves as a sophisticated method within this holistic security approach, offering dual benefits: it safeguards confidential data and creates a deterrence effect. While systems such as DLP and Digital Rights Management (DRM) are effective in curbing unauthorized actions and tracking illicit access, they fall short in fully securing documents. Within any company, sensitive assets—ranging from contracts to intellectual properties—are prone to exposure by insiders who, despite having legitimate access, may exploit this information.
The invisible watermarking technology by G-71, known as invisible watermarks or invisible fingerprints, is pivotal in overcoming these security gaps. Unlike traditional visible watermarks, invisible watermarks use a steganographic approach to embed unseen modifications into documents. This advanced feature of invisible watermarking allows the generation of trillions of distinct copies of a single document page, facilitating large-scale, secure document distribution tailored to individual users.
Additionally, G-71’s invisible watermarking technology extends its protection to printed documents, ensuring that invisible watermarks remain intact even in printed form. This critical feature of invisible watermarking allows organizations to trace the source of any leaked documents, reinforcing security measures.
The deployment of invisible watermarks is seamlessly integrated and transparent, automatically applying invisible watermarking based on preset criteria. This could range from applying invisible watermarks to every document within an organization to targeting specific departments or selected employees.
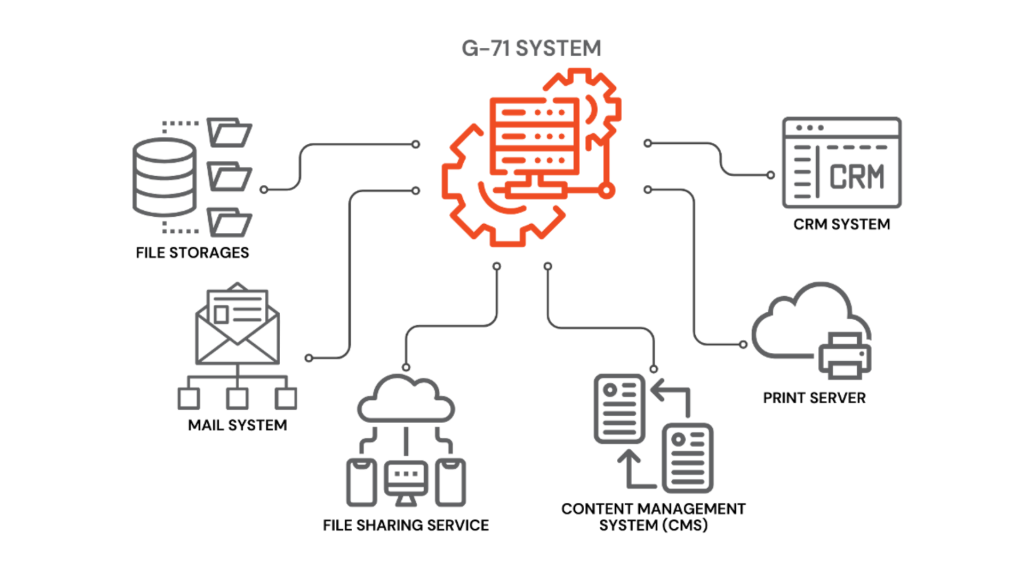
G-71’s invisible watermarking can be seamlessly integrated with existing organizational systems such as email servers, printing systems, document management systems, and cloud storage solutions like MS 365, enhancing the existing security infrastructure.
Another significant benefit of G-71’s invisible watermarking solution is its cost-effectiveness. The solution offers a fixed pricing model without limitations on the number of users or documents, making invisible watermarking accessible for businesses of all sizes.
For more details on how G-71’s invisible watermarking can fortify your company’s data security, click here.





